
At INCIDE we provide our consolidated expertise in security incidents management and our deep adversaries knowledge at our client’s disposal. This is achieved through top-quality managed cybersecurity services that allow them to reduce the probability of suffering an incident as much as possible.
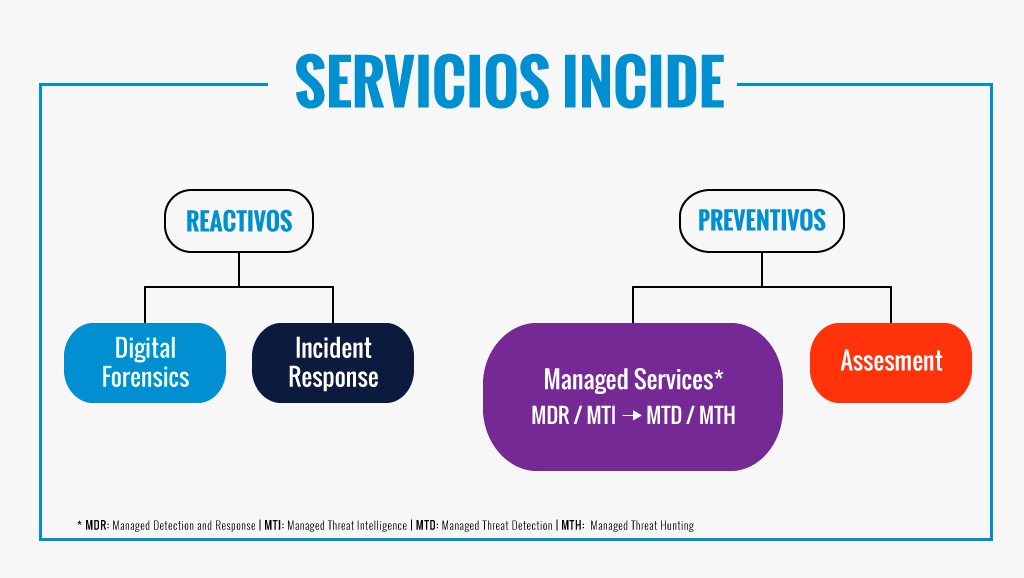
We offer the service MDR INCIDE [1] which allows us to operate and contain advanced threats. The service MTI INCIDE [2] allows us to keep ahead of the use of abusive information on account of the attackers. And, lastly, the services MTD [3] & MTH [4] INCIDE include proactivity as an engine of threat management.
[1] MDR = Managed Detection and Response [2] MTI = Managed Threat Intelligence [3] MTD = Managed Threat Detection [4] MTH = Managed Threat Hunting
MDR
The MDR service offered by INCIDE, through its strategic partnership with CrowdStrike, manages the security of the endpoint and takes part autonomously when security alerts and incidents arise. Our expertise in incident response allows us to constantly investigate and apply new containment measures to minimize the likelihood of an incident.
EDR Operation
Forensic investigation
Incident response and containment.
Contact us
MTD
The MTD INCIDE service is a step forward in enhancing detection and response capabilities. We use the knowledge we possess regarding cybercriminals and adversary techniques gathered during the incident investigations we carry out on a daily basis. It serves as a base to test them on the client's infrastructure. Subsequently, we analyze the result and, if necessary, suggest improvements for detection and blocking. This continuous improvement cycle allows us to overtake and be surpassingly ready in terms of defense once the attacker arrives.
Advanced attack simulations in controlled environments
Imminent threats assessment
Design of customized alerts
Contact us
MTI
The Threat Intelligence service offered by INCIDE, through its strategic partnership with Blueliv, monitors the deep web and malicious internet forums for credentials that have been stolen from organization members. The main objective of this is to identify and neutralize the potential malicious use of these to compromise the organization’s security. The domain monitorization prevents CEO frauds, BEC (Bussiness Email Compromise) attacks among other frauds, as well as spearphishing link actions or other brand abuses.
Prevention of the use of stolen credentials
Prevention of fraudulent use of domains
Detection of compromised information
MTH
The MTH INCIDE service is a proactive approach towards detecting attackers that might have violated the client’s systems even though we may not be aware of it. For this purpose, we formulate the attack hypotheses of a given adversary, and actively search for IoCs and attack techniques. The main goal is to detect possible compromises of the systems in order to contain and eradicate this threat. This leads us to improve in terms of detection and containment capabilities against this type of attack
Identification of latent compromises
Active search for IoCs and adversarial techniques
Early containment and eradication and enhanced detection
Contact us

We provide reactive services (security incidents, digital investigations, computer forensics) and preventive services (preparation of personnel and systems to effectively address future attacks, which is one of the most important fields of cybersecurity).
Response to security incidents
Have you detected a possible security breach? Can not access your systems or files? Have you suffered a loss of data?
Contact usInvestigation (of internal fraud) in digital environments
Have you suffered an internal fraud? Have you received threats or extortion? Have you detected any disloyalty? Do you need to carry out an investigation and find out who, what, when, why and how?
Contact useDiscovery
Do you need to know who has exchanged certain information in your organization? Do you suspect that certain information about your organization has been leaked?
Contact usComputer expert and ratification in court
Do you need to present evidence in a judicial process or evaluate an expert report from the opposing party? We have dealt with thousands of cases and conducted hundreds of expert reports with 100% acceptance of evidence in the judiciary.
Contact us
Incident response consulting
Do you need to evaluate and prepare your systems and personnel to optimally address future security incidents?
Do you have the necessary logs to carry out a correct investigation?
Contact usRemote response systems to incidents
Do you have the necessary tools to connect to remote computers in your organization and obtain the necessary forensic artifacts? Do you have a laboratory to process these devices in an agile way?
Contact usConsultancy
We provide advice on cybersecurity based on our professionalism and extensive professional experience in the areas in which we consider ourselves experts.
Contact us
There are different types and different approaches to carry out security audits. At INCIDE we base security audits on internationally recognized standards, such as OSSTMM, NIST SP 800-115, OWASP, MITRE ATT&CK Matrix, among others.
Red Team
The objective of a Red Team exercise is to test the level of detection of attacks of the Blue Team (Team of defense of the organization). For this, the Red Team carries out an attack to compromise the organization and without prior knowledge of the attack the Blue Team should be able to detect, identify and contain the threat. The key to these exercises is to be able to share ideas and solutions the level of detection against advanced threats
External hacking
An external hacking is an intrusion test in which points of entry that could allow an attacker access to privileged information from outside the systems of the organization are searched. The objective is to identify points of improvement in the systems of the organization.
Contact usInternal hacking
An internal hacking is an intrusion test in which they search for entry points that could allow an attacker access to privileged information from within the systems of the organization. The objective is to identify points of improvement in the systems of the organization.
Contact usEndPoint Audit Office
Most security commitments begin with an external commitment, generally through an email or visited link, of the team of a user of the organization. An EndPoint audit is an exhaustive audit of a standard equipment of the organization in which different standard vectors are tested to evaluate the protection measures of said EndPoint before different types and levels of threat. It is usually an ideal test if you want to evaluate different EndPoint solutions (AntiVirus, EDRs or other agents).
Contact usPerimeter Audit
It is the ideal complement to the EndPoint audit, given that by means of this test it is possible to exhaustively evaluate the detection level of the perimeter systems against different types of threat.
Contact usSocial engineering
The effort is concentrated in this case in the preparation of sophisticated attacks of social engineering to see what is the degree of alertness and preparation of end users against this type of attack techniques.
Contact usWiFi Audit
Security review of the organization's WiFi infrastructure and captive portals.
Contact usIncident simulations
The objective of these simulations is to evaluate the degree of compliance with the incident response procedures of the organization. To do this, a series of incident typologies are chosen and the response of the organization is studied.
Contact usGeneral security audit
The general audit of security is an audit indicated for those companies that want to start working security and that still do not have a security master plan or defined security projects.
Contact us